
This article is the second of a two-part series on genomic data. Part One, published in Issue 3 of Health21 magazine, http://health21initiative.org/article/precision-medicine-privacy-cybersecurity, laid out key issues affecting genomic data and technology challenges. Part Two offers an “additive” model to current regulations on genomic data to provide further protections along with key recommendations that include adoption of a higher standard of security and privacy protection for genomic data.
As noted in Part One of this article, the Genetic Information Nondiscrimination Act of 2008 (GINA) required modification to the Health Information Patient Protection Accountability Act (HIPAA) of 1996 to include genomic data as protected health information (PHI). Such inclusion is beneficial. However, simply categorizing genomic data as PHI data is not sufficient as protections afforded under HIPAA for PHI (health record information) do not account for such issues as multi-generational implications, informed consent, breach notification, etc., if these genomic data are breached. In short, genomic data requires a higher level of protection than traditional PHI.
Federal policies and laws do a reasonably thorough job on cybersecurity aspects of protecting health data. However, a gap exists regarding discussing HIPAA and the implications of this legislation on genomic data. Part Two attempts to fill the void.
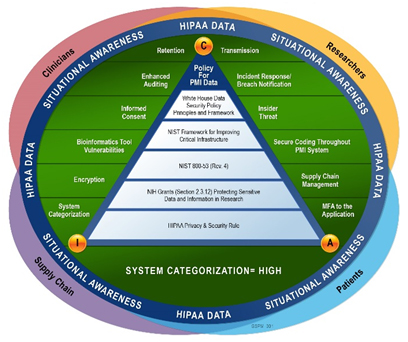
Figure 4: Genomic Privacy and Security Framework (GPSF)
The Model
Since genomic data has greater implications than traditional PHI, it must have more stringent privacy and security controls. Simply placing the same controls that exist for protecting electronic health records (EHR) data is not sufficient in this environment due to many nuances like storage, retention, generational implications, privacy considerations and the like. Therefore, Figure 4 introduces the Genomic Privacy and Security Framework (GPSF).
As Figure 4 illustrates, GPSF consists of several components. The triangle represents current policies for PMI and how confidentiality, integrity and availability (CIA) are proposed by federal and White House guidance. Outside the circle, primary “actors” – clinicians, researchers, supply chain and patients – are noted. The blue circular “band of protection” for HIPAA data starts with situational awareness and then moves to areas currently absent in discussions unique to genomic data.
Suggestions to enhance current policy when handling, transmitting or storing genomic data are addressed thoughout this article. Specifically, researchers on this article are advocating a move to de-identified data sets for genomic data whenever practicable. However, de-identification of genomic data must follow acceptable standards to ensure the genomic data cannot be re-identified. Recent cases exist where reidentification was shown to be possible; therefore, extensive care should be taken in determining de-identification standards (HHS offers their guidance on such standards)[1].
No model will absolutely provide assurance of prevention of a data breach. The GPSF model, although considered comprehensive in nature, holds that same limited assurance. Cyber criminals exist who strive to find the path of least resistance to breach the system. Therefore, the GPSF model is not offered as “fool proof;” however, it does offer a higher level of data protection than current suggestions for securing the human genome.
System Categorization
The Federal Information Processing Standards (FIPS) Publication 199, of the National Institute of Standards and Technology (NIST), develops a series of standards for categorizating information and associated information systems. Researchers for this article are of the belief that following the formula provided by FIPS 199 for categorizing information systems around CIA results in a FIPS categorization of “High” for data within the PMI data system (genomic data).
- SC EHR Data = {(confidentiality, moderate), (integrity, moderate), (availability, moderate)
- SC Genomic Data= {(confidentiality, high), (integrity, high), (availability, moderate)
- SC PMI System= {(confidentiality, HIGH), (integrity, HIGH), (availability, MODERATE)
The above categorizations for confidentiality and integrity were based on a set of genomic data realities that include:
- Genomic data can be stored and used indefinitely;
- Genomic data serves to inform individuals and families on inheritied, mutated or enviornmental conditions, “some of which are unexpected given personal or family history;”
- Genomic data can yield uncertain or unclear risks (genetic warfare, etc.);
- Genomic data, as technology progresses, can be reinterpreted and altered throughout time (i.e., gene editing technology. such as CRISPR, an acronym for Clustered Regularly Interspaced Short Palindromic Repeat, which refers to the unique organization of short, partially palindromic repeated DNA sequences found in genomes of bacteria and other microorganisms);
- Housing genomic data raises privacy concerns because risk of re-identification is plausible;
- Genomic data is pertinent to family members in regards to reproductive decision-making [14].
Collectively, this set of genomic data realities lead article researchers to categorize genomic data following the FIPS 199 “High” rating. The risk of exposure of genomic data exposes too many individuals, and the compromise of said data can be incredibly sensitive. The genomic health IT system should be designed adhering to security and privacy requirements, and implementation with the highest level of controls enabled to protect the intellectual property of the system. However, article researchers offer a cautionary note that through categorization to a high system, by requirements, all systems that connect also will become a high system. This can have significant resource implications. Any agency, institution or organization considering enhanced system categorization should make such a decision based on risk in consultation with their chief information security officer (CISO) and take all elements around that risk into consideration prior to implementation.
Encryption
A misnomer exists that HIPAA law mandates encryption of PHI; however, this is not the case. It is recommended as means for safeguarding electronically transmitted PHI. If an organization is unable to do so, it must state why and what alternative safeguards are outside encryption. Within the GPSF data security model, article researchers suggest mandatory encryption (FIPS 140-2) for the Precision Medicine Initiative (PMI) data in transit (i.e., transport layer security) and at rest in the database (AES 256-bit encryption). All devices storing or transmiting genomic data also should require encryption (e.g., laptops, tablets, cell phones, USB drives, etc.).
The encryption plan will include everything from authentication and PKI to utilizing industry-prescribed encryption algorithms. The encryption plan will map the encryption utilized for data in motion and at rest. It is our position that genomic files require encryption at rest and in motion, thereby ensuring genomic files and associated data about a patient are adequately protected.
There are several types of genomic files to be considered for encryption. Table 2 shows the various types of genomic files from a bioinformatics perspective to genetic reports about an individual’s DNA that should be encrypted:
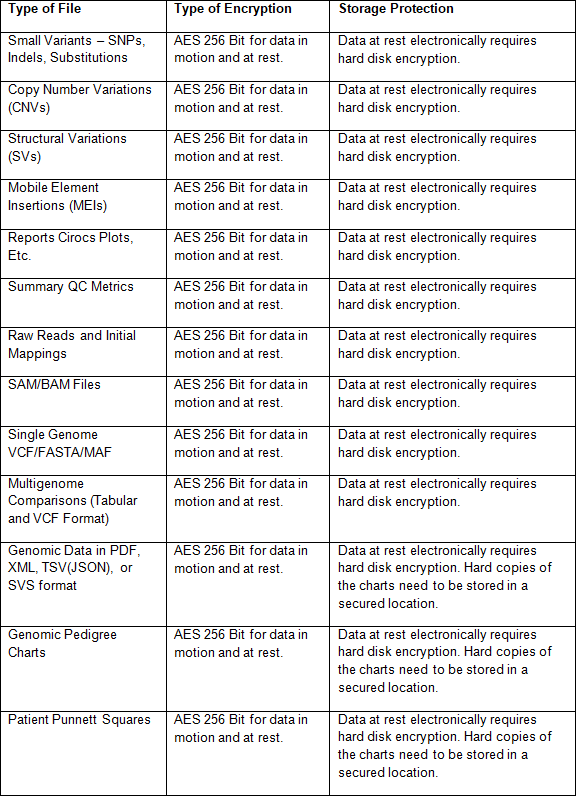
Table 2: Genomic Data Files for Encryption
There are a number of cryptographic solutions in the market as well as rapidly advancing technology (e.g., Homomorphic Encryption or Honey Encryption) that is making encryption less burdensome for users (researchers, clinicians, etc.). This research is not suggesting one means of encryption over the other as use cases dictate cryptographic options. However, the key point is that genomic data must be encrypted in transit and rest. The means of achieving this are varied and the organizations’ security professionals can make specific recommendations.
Bioinformatics Tool Vulnerabilities
As PMI starts to emerge and become more practical in clinical settings, there will be an increased need to ensure bioinformatic tools are hardened and secure coding is applied. PMI and telemedicine will increase health IT requirements for more robust and easier-to-use bioinformatic tools for reviewing, analyzing and sharing genomic data. There will be a demand for these tools and technology to create better output with smaller files or output to specific fields in a database table. As these demands for better tools come to fruition, a steadfast requirement will exist to ensure these tools are secure and provide defense-in-depth.
Precision medicine and genomic files are a new frontier for many in the health IT industry. As stakeholders learn about this new endeavor and how PMI systems work, users also can expect hackers will be paying attention and looking for vulnerabilities to exploit. Several online resources, homegrown tools and projects exist that should review their security and privacy posture for the code on these sites and in the project systems. It is important to run the code through security code analysis scanners to determine the security risk of the code. Securing bioinformatic tools will be key in protecting the PMI system.
Informed Consent
Genomic data falls above the domain of PHI. Therefore, all HIPAA regulations become applicable and research requirements outlined by NIH, the Common Rule and FDA requirements for federally funded research (www.genome.gov) along with suggestions within this article should be included. It should be noted that informed consent can be a unique challenge within genetic and genomic research [15]. HIPAA mandates researchers working within HIPAA-covered entities and, by defacto, their business associates must obtain informed consent before using or disclosing patient/participant individually identifiable health information [16]. Given these requirements for patient privacy and protection of research subjects, informed consent is an issue not typically molded into a security solution. However, given the nature of genomic data, it must be considered as part of the privacy solution.
With respect to research studies[2], informed consent applies to the following: (1) the individual’s decision to disclose personal data; (2) decisions about controls on access to data; and (3) decisions about appropriate uses and what constitutes “misuse” of data. Relevant law and regulation, including the HIPAA Privacy Rule, GINA and Common Rule, govern aspects of these components.
A need exists to consider modification of Informed Consent requirements when genomic data is involved. Informed Consent issues in those cases need to consider implications to family members. However, this might not be applicable in research settings, yet applicable from a PMI perspective.
Enhanced Auditing
A PMI system must require use of audit logging. Audit logging will help track users’ activity to a record, archive activity performed with the record (along with date, time and the account) and store all information in a secure audit repository. Genomic data is very sensitive HIPAA information and warrants detailed auditing to protect the data on a continuous basis. Audit logging also can provide alerts when rules are triggered for further investigation and provide an excellent forensic trail. It provides and enforces policies in place of the audit logging application. Additionally, audit logging for a PMI database or data warehouse provides a secure environment that is tamper resistant.
As a part of the audit logging requirement, a database firewall also should be implemented and interaction to the database and activity audited. Along with audit logging, the database firewall can review sequel (SQL) statements and queries to the database. Reviewing SQL statements for nefarious activity and SQL injection is crucial in this day and age, and will help protect the PMI system from hackers infiltrating the database and preventing confidentiality and integrity issues of genomic data.
The combination of audit logging and database firewall provides audit analysis and collection, monitors SQL traffic, provides security event reporting in both areas and facilitates whitelisting and blacklisting. PMI systems warrant audit logging and database firewalls as security requirements for the PMI system. These two security features should be architected into the initial design of the system.
Retention
Given whole genome sequencing will produce a staggering amount of raw data, and physicians/researchers still do not appear to know the full data to select (or its meaning) for a patient, an acceptable retention plan should be created in advance of utilization of genomic data. The PMI field will continue to develop and collect repetitive DNA samples as those advances occur. Storing existing DNA becomes a necessity, and secure retention strategies must follow. This storage of massive amounts of data brings signifiant challenges for rapid retrieval and analysis of retained genomic data and can compromise CIA of data as well as significantly hinder performance issues. Given current informatics, systems cannot efficiently store genomic data allowing for efficient search, analysis and sharing across health systems. DNA will need to be stored for protracted periods while technology catches up to the still unfulfilled promises of PMI data. At present, advances in sequencing technology have surpassed current ability to store and analyze said data.
Since the goal of allowing transfer of stored genomic raw data sets into the healthcare system has yet to be fully realized, this leaves security analysts reviewing solutions like cloud services to loosen the burden on ill-equipped data centers to meet this clinical challenge. Companies like Panasas and DDN are making great strides in data storage, thus significantly improving “big data genomics.” Additionally, research in next-generation sequencing (NGS) will reduce cost and time for reading DNA of large populations and reduce strain from a storage and retention perspective. However, all these advances must be paralleled with privacy and security for ensuring HIPAA compliance.
Long-term retention leads to secure storage concerns, where storage requirements will most likely exceed 50 years. Genomic data is PHI data and is associated with a patient’s EHR file for a lifetime or beyond, particularly when factoring generational family health. Thus, this makes it more valuable to cybercriminals than traditional PHI. Long-term rentention policies need to consider the life cycle of the PMI system and collection of genomic data to the point the system becomes a legacy system itself. Genomic data will span multiple generations, and the PMI retention plan ought to consider genomic data beyond 10, 20, 50 and 100 years.
Hard drive capacity also will have to be addressed to accommodate influx of genomic data in regards to precision medicine. Storage of genomic files may be problematic for a few years since genomic files are voluminous. However, as genomic data becomes more mainstream in precision medicine, IT professionals and companies will create alternative means for storing data and new ways to convert DNA specimens into genomic data. Until this happens, it is best to develop a hard drive capacity plan for the entire life span of the bioinformatics project.
Genomic data, like other health data now part of the PMI data chain, falls within a designated record set (DRS) and must be afforded equal HIPAA protection as other PMI data, including while stored in the laboratory. This last part adds a degree of privacy scrutiny laboratories must be aware of and be ready to absorb the implications of. The rationale is there have been changes to the Clinical Laboratory Improvement Amendments of 1988 (CLIA), thus allowing a patient rights to completed laboratory reports. This seems to be applicable if the research laboratory is affiliated with the covered entity as part of the continuum of care for DNS, thereby making it obliged to comply with HIPAA. Of course, there are exceptions, and to learn more about laboratory implications, visit http://www.ncbi.nlm.nih.gov/pmc/articles/PMC4308037/.
Transmission
Much like a retention plan, considerable forethought is required around transmission standards for genomic and EHR data (facsimile, e-mail, file sharing, disaster recovery sites, etc.). Most frequently, due to file size, electronic transmission of genomic data will be largely restricted to file-sharing activities and not e-mail. However, the data security plan[3] should lay out requirements for electronic transmission of PHI Personally identifiable information (PII) data over the Internet (including e-mail), file transfers or other data transfer modalities and include end-to-end security that is inclusive of additive controls suggested in this paper.
In order to understand transmission of data, a transmission/encryption diagram ought to be created to show the path of genomic and PMI data through the system and supply chain. This would require a line in the diagram showing the encryption being used, types of ecnryption and open ports on servers. Understanding how data is transmitted and stored at rest is crucial in determining what encryption methods are faciliated in the PMI system.
Incident Response/Breach Notification
An incident response plan is a basic element of any security plan. However, with genomic data, careful consideration should be given to breach notification procedures. If under research protocol, take into account that NIH (or sponsoring research facility) will require notification of security breaches within a specific timeframe. Also, with the potential of reidentified genomic sequence data, responsibilities for breach notification can become unclear.
It is recommended a specific genomic incident response (GIR) policy be created in the event genomic data is exposed. The GIR policy will address what needs to be done, if genomic files are involved in an incident. Policy will provide direction on who needs to be contacted and when and steps involved to address incident response. Typically, systems have a security and privacy policy, but given the nature of the genomic data, it is recommended to have a specific incident response policy for genomic files.
Insider Threat
When dealing with highly sensitive data like genomic data, there is a concern about insider threat in the PMI system and supply chain. Insider threat is defined as an employee, possibly trusted, who intentionally harms the system for financial gain or maleficent reasons (e.g., disgruntled employee). Many cases exist where an employee compromises a system for his/her own greed and monetary gain, or state-sponsored espionage. A PMI system housing genomic data will be a prime target by both state-sponsored entities and hackers for black market or dark web financial gain.
A Department of Defense (DOD) directive exists to fully institute an insider threat program for cleared contractors. Given PMI systems with genomic data ought to have a FIPS 199 rating of HIGH, a PMI system must implement an insider threat program to ensure protection of sensitive HIPAA data being stored in this system. There should be a policy and procedure for an insider threat program where continuous monitoring of employee activity can detect and deter risky behavior, and identify potential nefarious activity on the PMI system and the genomic data stored in the system.
Secure Coding Throughout the PMI System
The PMI system should follow secure coding practices from end-to-end. Vendors in the supply chain have equal responsibility to ensure software they develop is secure, be it commercial off-the-shelf (COTS) software, open source software and custom-built applications for a PMI system. A secure code development life cycle should be adapted and followed through continuous monitoring to ensure security and privacy of the system is hardened and remains hardened through subsequent releases and patch updates.
Any code written for a PMI system, including bioinformatic tools, ought to be hardened through secure code. This includes secure code reviews, threat tree modeling, secure static code analysis, dynamic code analysis and penetration testing. Security reports ought to be remediated following the appropriate time frames from highs (within 10 days), moderates (within 30 days) and lows (within 90 days). Lows must be mitigated because hackers know most federal agencies and corporate companies only focus on mitigating highs and moderates. Low vulnerabilities are considered low-hanging fruit that hackers will look to exploit and gain entry into the system.
Both situational awareness and continuous monitoring should be followed for PMI systems to ensure proactive security for applications. Keeping a PMI system hardened and current with patches is a requirement when considering the increased skill sets hackers exhibit. As nefarious actors gain sophistication in their malware creation, securing code in a PMI system is paramount. It will only be a matter of time before hackers target the PMI system for the vast treasure trove of genomic data, much like they have with EHR systems.
Supply Chain Management
When considering supply chain, there are many elements to a PMI system that are new to the health IT field. Vendors for a PMI system can include but may not be limited to: BioBanks, genetic interpretation services, laboratories, hospitals, individual doctor offices, genetic testing services, genomic counselors, government projects and academic projects that may share data. Any one of these vendors in the supply chain can pose a significant threat to the PMI system. All vendors and their employees must be thoroughly vetted to handle PMI data and take HIPAA and incident response training.
Several documents exist that can help to ensure protection of PMI data with vendors in the supply chain, to include business associate agreements, service-level agreements, non-disclosure agreements, signed rules of behavior for staff and consistent HIPAA and incident response training. PMI data, specifically genomic data, is HIPAA data and warrants all protections from the HIPAA law. Each vendor in the supply chain must be HIPAA compliant and ensure their health IT environments are secured and adhere to continous monitoring. The prime contractor must verify security and privacy compliance of all subcontractors prior to allowing exposure to PMI data. Possibly, the industry can create a consortium of “trusted third parties” that become certified in handling genomic data in a secure manner.
In regards to staff, each vendor in the supply chain for a PMI system ought to perform a rigorous background check on employees, and an insider threat program must be instituted across the supply chain. Employees of the system are considered the first line of defense in protecting genomic data, so enhanced emphasis with vendors must occur to facilitate a robust HIPAA program.
Multifactor Authentication (MFA) to the Application
PMI systems should be treated as FIPS 199 High systems due to the nature of genomic data stored. The PMI system should be architected from the start to provide multifactor authentication (MFA) for all users, including patients. Former President Obama clearly articulated he would like to have patients accessing their PMI records with genomic data. Clinicians, researchers and medical staff also may require access as well as health IT staff, which is comprised of database administrators, software developers, testers, security staff, network engineers and any other administrator. Regardless of access priviledge (e.g., read, write or delete) all users of a PMI sysem should be required to use MFA. Users of a PMI system, including access privileges, are depicted in Table 3.

Table 3 PMI Users and Environments
MFA provides more secure access to the PMI system. It will help deter unauthorized access to the PMI system at any one of four identified levels noted in Figure 3, due to lack of knowledge of the user’s credentials of something the user knows or possesses (part of the MFA requirement).
Utilizing MFA for a PMI system can reduce online fraud, identity theft and potential industrial and state-sponsored espionage. The PMI system must require MFA and be architected at the beginning to ensure correct implementation of MFA. The security requirement for MFA will include MFA to the application, servers and network equipment. Patients and clinicians access the PMI system via use of a personal identity verification (PIV) card (HSPD-12) or token. Likewise, administrators accessing the system should be required to use a PIV card or token/VPN for access to servers and software.
Based off a newly released U.S. Office of Personnel Management (OPM) Breach report, all users of a PMI system and supply chain ought to be required to use MFA to access a PMI system with genomic data [17]. MFA was the number one recommendation from the OPM Breach Report to ensure only those authorized to access a server or application are properly authenticated and have the right access control to genomic data. Using PIV cards or RSA tokens should be the only means for accessing the PMI system.
Genomics and the Future
Genomic research is moving at a rapid pace. Exciting things are occuring in the field, which takes on a sci-fi approach, but plausible nontheless. The future may hold even more cybersecurity challenges as scientists look at the storage potential of DNA itself or the field of pharmcogenomics where medicines are catered to specific genomic data.
Using Genomic Structures to Store Data
The futuristic opportunity to store data in DNA provides many wonderful possibilities in healthcare. However, an equal number of security and privacy concerns emerge. Research is being conducted to store data in DNA, the human brain and glass, which can subsist for 2,000 to billions of years. The technology being researched will definitely revamp the way stakeholders look at data retention and legacy systems.
Last year, Popular Science Magazine reported on research involving DNA being utilized to store data, which can be preserved for more than 2,000 years. The article referred to a presentation at the 250th National Meeting and Exposition of the American Chemical Society (ACS). The experiment demonstrated encoding of 83 KB of text into DNA. Researchers had a DNA strand that contained a 10th century literary work “The Method of Archimedes,” and it also contained a charter from 1291. The significance of the research proves DNA can store text data and survive throughout a long period of time.
Further research will be conducted in this field to provide alternative storage solutions using DNA rather than conventional methods (e.g. tape backups, conventional hard drives, etc.). Researchers surmise that DNA can possibly store, in theory, more than 300,000TB of data. Additionally, based on scientists obtaining DNA from hundreds of thousands of years, it is plausible DNA with stored data could persist with greater longevity than previously anticipated [18].
Subsequent discussion has occured with scientists about storing information in the brain. However, there have not been any viable experiments to prove the brain could be tapped to store text data, and the brain material does not have the longevitiy of DNA[19]. Further research exists about storing data, which could include genomic data, through creation of glass cubes that can resist extreme heat and also have a long life span. Scientists developed a new data storage technique that can store, through laser writing (i.e., nanogratings), 360TB of data on a glass device, which can persist for billions of years. When considering the future of DNA and storing data articles, researchers are looking at extremely long-term storage rates where genomic data would last indefinitely. Therefore, security professionals must maintain due diligence in keeping up with technology to ensure these data are not compromised throughout the lifespan of storage, regardless of the means.
Pharmacogenomics
Another field to consider in regards to genomic data is pharmacogenomics [20], defined as the study of how drugs and DNA respond to one another. The concept is to develop drugs that are specially tailored to DNA makeup for better treatment and reaction to medication. For example, new medicines could be tailored for cancer patients with a specific DNA rather than one medicine for all patients. Pharmacogenomics is the marriage of pharmacology and genomics.
All HIPAA security and privacy concerns noted in this article equally apply to a pharmacogenomics system where patient genomic data is stored in a database for drug manufacturers and pharmacists tailoring medicines to a patient’s genetic makeup. The research data, medicines and genomic data will require security controls be applied at a FIPS 199 rating of HIGH as well. Concern exists regarding protecting this data from nefarious activity (e.g., bioweapons).
IOT Devices
As “Internet of Things” (IoT) devices increase in popularity, PMI systems will be designed to include wearable devices that could relay genomic data from the wearable device to the PMI system. Other data also could be transmitted, to include patient vitals, eating, sleep and exercise habits. All these data points from the patient can be applied to the patient’s precision medicine treatment plan. Privacy concerns with this technology are already surfacing within the healthcare field, and all HIPAA safeguards should be applied to protect the data for any device designed for collecting and transmitting health information.
Conclusion
There is no reversing the path of moving to precision medicine. With the advent of technology advancements in this field, vigilence must be paid to ensuring genomic data is appropriately secured for reasons outlined in this article. However, if stakeholders simply rely on current policy, they will fall short in offering true protection to genomic data sets as those policies pay little focus to HIPAA implications regarding genomics.
It is suggested by article researchers that the path forward be paralleled with additional privacy and security controls outlined in the model presented herewithin. By doing so, the authors believe the rapid advances and promising treatments made available by coupling genomic data within the electronic health record will not become rapidly stymied by the public should a breach occur.
Lastly, this article discusses the need for a multitude of additional plans that should be created when handling genomic data (data storage, encryption, incident response, transmission, data security and privacy, etc.). These plans serve a greater purpose and should not be created in isolation by the security team. The goal of emphasizing the need for these additional plans is for the collaborative team to think through an enhanced security posture, following the GPFS model, and to agree on processes and procedures to protect security and privacy of genomic data entrusted to them. The case has been made in this article to show signficant risks associated with genomic data, with current policy falling short (particularly on the privacy side), thereby requiring this additive source.
References
- https://ghr.nlm.nih.gov/primer/precisionmedicine/definition
- Payne, Thomas H. et al. “Report of the AMIA EHR 2020 task force on the status and future direction of EHRs.” Journal of the American Medical Informatics Association. May 29, 2015. http://jamia.oxfordjournals.org/content/early/2015/08/14/jamia.ocv066.
- http://www.statewatch.org/news/2015/may/usa-crs-geomonic-data.pdf
- 4. https://www.genome.gov/27026588/informed-consent-for-genomics-research/
- July 18, 2003: HIPAA Authorization for Research. National Institutes of Health
- http://www.statewatch.org/news/2015/may/usa-crs-geomonic-data.pdf
- Michael Snyder. “Genomics and personalized medicine: what everyone needs to know.” Oxford University press. 2016
- 8. https://www.technologyreview.com/s/509901/study-highlights-the-risk-of-handing-over-your-genome/
- Jennie Dusheck. “Stanford researchers identify potential security hole in genomic data sharing network.” 2015. Retrieved from https://med.stanford.edu/news/all-news/2015/10/standford-researchers-identify-potential-seuciryt-hole-in-genmic.html.
- William Ferguson, 2013. “Attacked database prompts debate about genetic privacy: Experts urge transparency and new regulations to protect DNA donors.” Scientific American, 2013, http://www.scientific.american.com/article/a-hacked-database-prompts.
- Elizabeth Joh, “DNA Theft: Recognizing the crime of nonconsensual genetic collection and testing.” Pages 665-700, Boston University Law Review, Vol 91, Number 2, March 2011.
- Mackenzie Foley. “Genetically engineered bioweapons: A new breed of weapons for modern warfare.”2013. Retrieved from http://dujs.dartmouth.edu/2013/03/genetically-engineered-bioweapons-a-new-breed-of-weapons-for-modern-warfare/#.V7EmpZgrKUk.
- www.cnn.com/2016/08/04/healht/elephant-tranquilizer-carfentanil-herion. Article written by Nadia Kounang and Tony Marco – “Heroin laced with elephant tranquilizer hits the streets.” Aug 25, 2016
- https://www.genome.gov/27026588/informed-consent-for-genomics-research/
- https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3216676/
- http://www.hhs.gov/hipaa/for-professionals/privacy/guidance/research/index.html
- https://oversight.house.gov/wp-content/uploads/2016/09/The-OPM-Data-Breach-How-the-Government-Jeopardized-Our-National-Security-for-More-than-a-Generation.pdf
- Alexandra Ossola. (2015) DNA can store your digital data for up to 2,000 years; stop throwing all your data into a digital black hole. Retrieved from: www.popsci.com/dna-data-storage-can-last- 2000-years
- Taken from: https://hacked.com/researchers-prove-ground-breaking-potential-dna-storage-digital-data/
- Michael Snyder. “Genomics and personalized medicine: what everyone needs to know.” Oxford University press. 2016
Footnotes
[1] HHS outlines two acceptable strategies “for deidentifying protected health information (PHI) in accordance with the HIPAA Privacy Rule (expert determination and safe harbor).” (Source: https://www.hhs.gov/hipaa/for-professionals/privacy/special-topics/de-identification/) An evaluation of the risks and benefits should be conducted.
[2] See https://www.everycrsreport.com/files/20150511_R44026_a4d4870f5a12c170796dec36b3a3dfcc8863e792.html for more detailed discussion in this area—the source of this portion of the informed consent section.
[3] Part of the data security plan should include a Genomic Data Sharing (GDS) Policy that covers the element of this report


